Memory virtualization solves the problem of how the processes inside the virtual machine access the memory on the physical machine.
GuestOS itself has a virtual address space, which is represented by GVA. The virtual machine thinks that it owns the entire memory space and uses GPA.
HostOS itself has a virtual machine address space, which is represented by HVA. The host itself has physical memory space, represented by HPA.
Well, the issue of memory virtualization has become a problem with the mapping of GVA-HPA.

The GVA-"GPA" is mapped through the GuestOS page table. HVA-"HPA through HostOS page table mapping. Therefore, as long as the mapping relationship between GPA and HVA is established, the problem of memory virtualization can be solved. However, this three-parameter mapping is inefficient.
Introduced a software simulated shadow page table and a hardware-assisted EPT page table.
Shadow page table: When GuestOS creates a GVA-GPA page table, kvm knows the HPA corresponding to the HPA and secretly records the mapping relationship GVA->HPA. When the subsequent GVA to GPA mapping is required, the HPA can be found from the shadow page table.
EPT page table: EPTP registers are introduced at the hardware level. Directly load Guest's CR3 into the host's MMU. At the same time, the EPT page table is loaded into the special EPT page table pointer register EPTP. In other words, GVA-"GPA-" HPA twice address translation is implemented by hardware.
2. OverviewWe know that after the 80386 introduces a protected mode, the memory space is divided into a virtual address space and a physical address space. Subsequent introduction of the page table mechanism, the virtual machine address sent to mmu, mmu check the TLB is not the case, in turn search the page table can find the corresponding physical address.
In the virtualization scenario, the situation is slightly more complicated and is divided into the following types:
1GuestOS virtual address (guestOS virtual Adress, GVA)
To put it plainly, the virtual address used by the process in guesses is the GVA, which is the address of the program access logical memory.
2guestOS Physical Address (GPA)
The physical address that Guestos thinks is also the address that the virtual machine mmu looks up in the page table. But it is essentially a logical address. It is a logic concept that comes after the introduction of virtualization. It must be mapped to the host's physical address by means of memory virtualization to access memory
3Host virtual address (HVA)
The virtual address in the host machine, the virtual address space used by the host process.
4 Host Physical Address (HPA)
Host real memory address, real physical memory space that can be accessed.
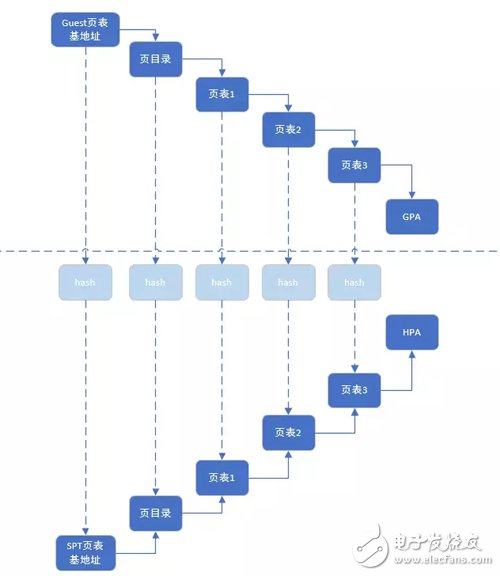
At this point, in the virtual machine scenario, how GVA-HPA is the work of memory virtualization. Among them, Qemu is responsible for managing the memory size of the virtual machine and recording the corresponding HVA address of the memory (because Qemu is a user-space process and cannot manage HPA). To convert to HPA, it is necessary to resort to the KVM kernel, that is, the Shadow Page Table (SPT). And EPT (Extent Page Table)
2.1 shadow page table
When Guestos builds a page table, KVM secretly creates a set of page tables pointing to the host's physical address. Each page table entry in the client has a shadow page table entry that corresponds to it, just like its shadow.
When the client accesses the memory, it is the shadow page table corresponding to the current page table of the client that is actually loaded into the host MMU. Thus, the real memory access can be realized through the shadow page table. The virtual machine page table and the shadow page table pass a ha. The table creates an association so that the guest physical address through the page directory/page table can quickly find the corresponding shadow page directory/page table in the hash list. When the client switches the process, the guest operating system will switch the process to be switched. The page table's base address is loaded into CR3 and the KVM will intercept this privileged instruction and perform new processing. That is, the base address of the shadow page table corresponding to the base address of this page table will be found in the hash table and loaded into the client CR3. When the client resumes running, CR3 actually points to the shadow page table for the new switch process.
2.2 EPT
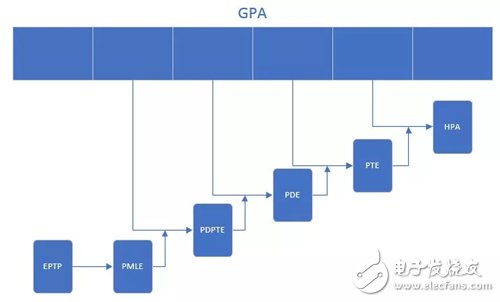
The EPT technology uses the EPT page table to implement another mapping from the physical address of the client to the physical address of the host based on the mapping of the client virtual address to the physical address of the client in the original client page table. Both address mappings are Automatically completed by hardware. When the client is running, the client page table is loaded into CR3, and the EPT page table is loaded into the special EPT page table pointer register EPTP.
During the conversion from the physical address of the guest to the physical address of the host, the client exits due to missing pages, lack of write permission, and the like, resulting in abnormal EPT. For the EPT page fault exception, the KVM first maps to the corresponding host virtual address based on the physical address of the guest that caused the exception, then assigns a new physical page to the virtual address and finally KVM and then updates the EPT page table to set up the client that caused the exception. The mapping between machine physical addresses and host physical addresses. For exceptions caused by EPT write permission, KVM is resolved by updating the corresponding EPT page table.
From this, it can be seen that the EPT page table is greatly simplified compared to the aforementioned shadow page table. Also, because the page fault within the client does not cause the client to quit, the performance of the client is improved. In addition, KVM only needs to maintain a set of EPT page tables for each client, which also greatly reduces the memory overhead.
3. Qemu to KVM memory management3.1 Setting hooks
Main(vl.c)==â€configure_accelerator==â€kvm_init(kvm_all.c)==â€memory_listener_register(&kvm_memory_listener,NULL); add kvm_memory_listener to the list of memory_listeners and associate address_spaces with the listener
3.2 Memory Object Initialization
Main(vl.c)==â€cpu_exec_init_all(exec.c)==â€memory_map_init(exec.c) The Qemu system memory is managed by system_memory, and the io memory is managed by system_io. staTIc MemoryRegion *system_memory.MemoryRegion can have sub-zones. The memory_lister handles the management of adding and removing memory areas.
3.3 Memory instantiation
Pc_init1(hw\pc_piix.c)==â€pc_memory_init Here we mainly allocate the entire memory area. Focus on the memory_region_init_ram method memory_region_init_ram==â€qemu_ram_alloc†(Get the HVA record of the memory) == “qemu_ram_alloc_internal==†ram_block_add (Generate a RAMBlock Add to ram_list , hva put into the host field) == "phys_mem_alloc ==" qemu_anon_ram_alloc == "mmap
3.4 VM-Exit Processing
Due to the exit caused by mmio, the related processing is as follows: kvm_cpu_exec==†case KVM_EXIT_MMIO==†cpu_physical_memory_rw==†address_space_rw==†io_mem_write
3.5 qemu to kvm Memory Call Interface
Earlier we talked about registering a listener and calling it when setting memory
staTIc MemoryListener kvm_memory_listener = {
.region_add = kvm_region_add,
Region_add==â€kvm_region_add==â€kvm_set_phys_mem
1 physical start address and length, search for established KVMSlot *mem area in kvm_state
2 if not found to create a slot
==â€kvm_set_user_memory_region†(informs the kernel to create a memory area) ==â€kvm_vm_ioctl(s, KVM_SET_USER_MEMORY_REGION, &mem)
3.6 KVM memory processing
Kvm_vm_ioctl==â€kvm_vm_ioctl_set_memory_region==â€kvm_set_memory_region==â€__kvm_set_memory_region Kernel also maintains a slot. The kernel-state slot management strategy is based on the user-space slot_id—slot-to-memory (kvm-â€memslots, mem-â€slot );
1 Get the Kernel-State Correspondence Structure by Slot in User State
2 According to the value in the slot and the value to be set, determine the category to operate
3 Operate according to the actions in 2
a.KVM_MR_CREATE: kvm_arch_create_memslot (made a 3-level page table)
b.KVM_MR_DELETE OR KVM_MR_MOVE:
Apply for a slot and temporarily save the kvm-memslots here. First, the id_to_memslot is used to obtain the memory to be inserted and the slot corresponding to the kvm is the slot. It is marked as KVM_MEMSLOT_INVALID whether it is deleted or moved. Then install_new_memslots, in fact, updates the value of the slots-generaTIon.
4. EPT related4.1 EPT initialization
Kvm_arch_init==》 kvm_mmu_module_init
1 establish pte_list_desc_cache cache structure
2 build mmu_page_header_cache cache structure, this structure is used for kvm_mmu_page
3register_shrinker (&mmu_shrinker); hooks when system memory reclaim is called
Vcpu_create==â€vmx_create_vcpu==â€init_rmode_idenTIty_map==â€alloc_identity_pagetable==â€__x86_set_memory_region
4.2 EPT loading
Vcpu_enter_guest(struct kvm_vcpu *vcpu)==†kvm_mmu_reload (Guest's MMU initialization, for memory virtualization)==†kvm_mmu_load==â€mmu_topup_memory_caches==â€mmu_alloc_roots--â€mmu_alloc_direct_roots(Build ept top according to the current vcpu paging mode The management structure of the page table ==â€kvm_mmu_sync_roots
4.3 gfn_to_page
This function handles the page number of the GPA to the HPA page structure:
Gfn_to_page=="gfn_to_pfn=="gfn_to_pfn_memslot=="__gfn_to_pfn_memslot=="__gfn_to_hva_many|hva_to_pfn=="hva_to_pfn_fast|hva_to_pfn_slow
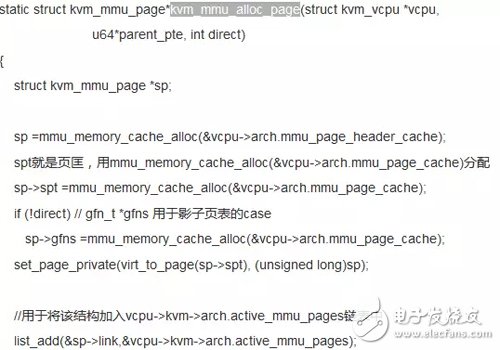
4.4 Allocation page table
Mmu_alloc_roots--"mmu_alloc_direct_roots--"kvm_mmu_get_page--"kvm_mmu_alloc_page
4.5 EPT vm-entry
1KVM_REQ_MMU_RELOAD--"kvm_mmu_unload--" mmu_free_roots
2KVM_REQ_MMU_SYNC--"kvm_mmu_sync_roots--"mmu_sync_roots--"mmu_sync_children--"kvm_sync_page--"__kvm_sync_page
3KVM_REQ_TLB_FLUSH--"kvm_vcpu_flush_tlb--"tlb_flush--"vmx_flush_tlb--"__vmx_flush_tlb--"ept_sync_context--"__invept
Enter the non-root mode, according to different events for memory processing.
4.6 EPT VM-exit
1 Set up cr3
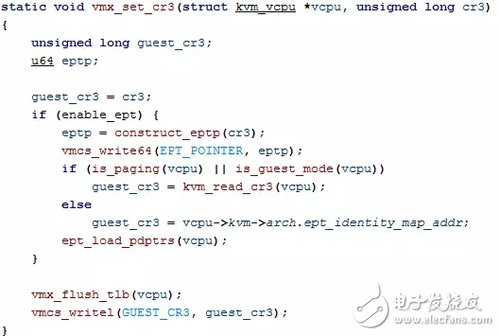
When mmu_alloc_direct_roots allocates arch.mmu.root_hpavcpu_enter_guest, it will call kvm_mmu_load==†vcpu-â€arch.mmu.set_cr3(vcpu,vcpu-â€arch.mmu.root_hpa) This function will request memory and use it as the root page table. At the same time root_hpa points to the physical address of the root page table. You can then see that the address of the cr3 register in vcpu is pointing to the physical address of the root page table.
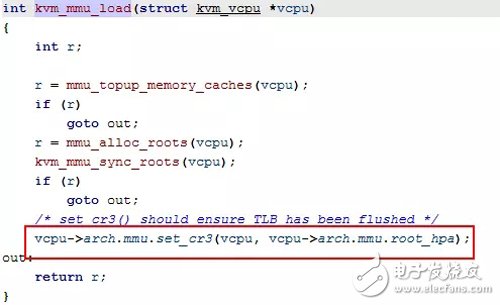
2handle_ept_violation
--"kvm_mmu_page_fault--"arch.mmu.page_fault--"tdp_page_fault
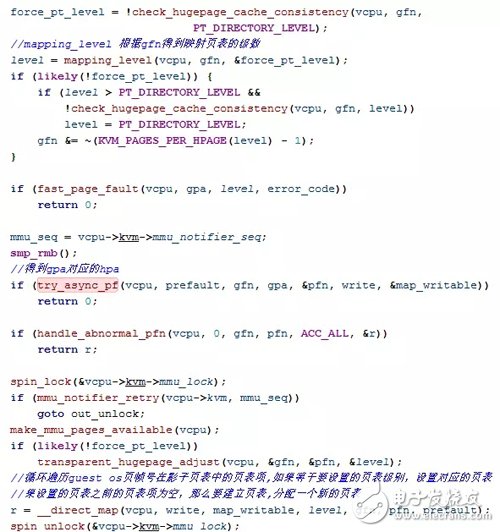
__direct_map This function is based on the gpa passed in. From the level-4 page table page, fill in the corresponding page table entries level by level. These are all for_each_shadow_entry(vcpu, (u64)gfn PAGE_SHIFT, iterator) This macro definition is implemented inside. The two situations are like this:
a. If the current page table page's layer (iterator.level) is the last level of the page table page, the page table entry is set directly by calling mmu_set_spte (more on this later).
b. If the current page table page A is not the last layer, but a middle layer (leve-4, level-3, level-2)
And the page table entry has not been initialized before (!is_shadow_present_pte(*iterator.sptep)) then you need to call kvm_mmu_get_page to get or create a new page table page B and link it to the page table entry corresponding to page table page A through link_shadow_page
4.7 EPT traversal operation
For_each_shadow_entry This is a macro defined in mmu.c to continuously traverse the page table hierarchy.
4.8 Shadow Page Table
Init_kvm_mmu==â€init_kvm_softmmu
In the above-mentioned ept process, according to the different parameters, there will be the general logic of different branches to be consistent. Needless to say.
Filter mesh refers to small aperture metal mesh or other materials with smaller apertures for a variety of different filtration, dust removal and separation requirements. They are widely used in shower panel, sanitary pipe systems, purifiers, electronic components, to remove contaminants or in applications, such as coffee machine, soya milk machine, to extract a filter cake. Because the metal mesh filters are one of the most durable filter media available, the material is mainly made of copper, iron, steel, nickel, stainless steel, alloy. It is acid resistant, alkali resistant, temperature resistant and wear resistant.
We customize diverse patterns metal microporous mesh with drawings provided by customers. We are equipped with professional metal etching equipment and exposure development equipment. Chemical metal etching filter mesh is a double-sided and simultaneous processing technology, which can make the product surface (positive and negative) smooth, without bumps, pits, burrs, warps, and flat mesh without deformation. Below are the advantages for customized metal filter mesh:
Flow Rate
One of the most significant advantages metal mesh has over most filter media used today is its ability to deliver an adequate flow rate. This is achievable as the wire diameter and mesh opening can be customized to perfectly match the contaminants you are filtering out, providing you with an enhanced level of filtration surface area.
Durability
300 series stainless steel is predominantly used. This helps create a filter that can withstand a wide range of impurities, pressure variations, and extreme temperatures without hindering the filter's accuracy. In addition, stainless steel is a very pliable material, allowing the filter to be formed to fit your filter system and hold its shape after several uses.
Accuracy
The weaving process used to construct mesh filters is heavily monitored from start to finish. As a result, the pore openings of the filter are exact and uniform throughout the filter. These precise pore opinings ensure that the end product, whether a filtered substance or a filter cake, is consistent and complies with industry standards.
Clean ability
As metal mesh features accurate pore openings, blinding and plugging are significantly reduced. This, combined with the enhanced flow rate, means system operators can clean the metal mesh easily. These two properties allow the mesh filter to be backflushed and purged of any unwanted debris with minimal pressure.
Metal Faucet Filter,Metal Coffee Filter,Metal Speaker Mesh,Customized Metal Filter Mesh
SHAOXING HUALI ELECTRONICS CO., LTD. , https://www.cnsxhuali.com
